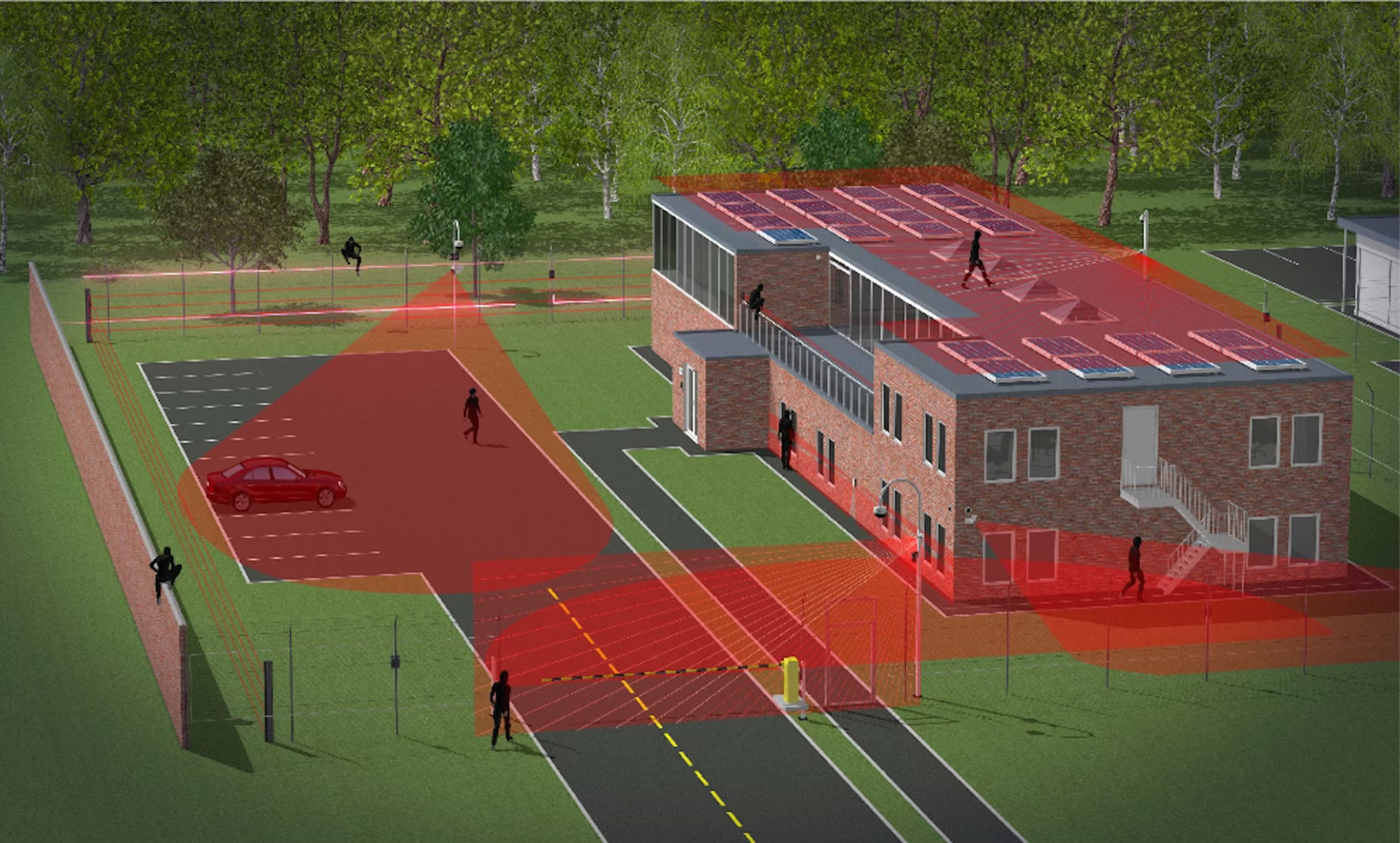
If you manage an office tower, mixed-use retail center, or industrial park, creating a Layered Security for Commercial properties is the fastest way to turn ad-hoc measures into a coordinated defense. A layered approach blends people, processes, and technology into concentric rings of protection—so a single failure doesn’t become a catastrophic breach.
What “layers” really mean in practice
Layering (often called defense-in-depth) is the idea that no one controlling—fences, cameras, access cards, or patrols—should carry all the risk. Instead, multiple controls overlap to deter, detect, delay, and respond. Professional bodies emphasize this approach because it forces adversaries to defeat several barriers in sequence, buying time for trained responders to intervene.
Start Layered Security for Commercial Properties with a risk-led blueprint
Before buying gear or hiring staff, anchor your plan in a formal risk assessment: identify critical assets, threats, vulnerabilities, likelihood, and impact; then prioritize controls by risk reduction per dollar. NIST’s well-known framework explains how to structure these steps and document decisions for executives. (Read more in NIST SP 800-30’s overview.) NIST Computer Security Resource Center
Outer layer: site perimeter and property lines
Goals: clear territorial definition, early detection, and standoff distance.
- Natural & built barriers: landscaping berms, CPTED lighting, anti-vehicle bollards, fencing, and controlled vehicle gates to channel access.
- Perimeter detection: pole-mounted cameras with analytics, thermal coverage for blind spots, and intrusion sensors at vulnerable segments.
- Wayfinding & policy signs: make rules visible (hours, visitor routing, no-trespass notices); clear expectations enhance deterrence and support enforcement.
- Mobile patrol patterns: randomized patrol routes increase unpredictability and visibly project authority—especially effective for large parking areas.
Entry layer: gates, docks, and lobby thresholds
Goals: control who (and what) crosses the boundary.
- Access control: card, mobile credential, or PIN at exterior doors and vehicle gates; anti-passback and automatic lock schedules by tenant mix and shift.
- Visitor management: pre-registration with QR codes, identity verification at reception, and temporary badges that expire.
- Dock oversight: integrated cameras, seal checks, and escort policies for contractors and vendors.
- Reception readiness: a trained concierge or officer with de-escalation skills; panic notification tied to radios, strobe lights, and intercoms.
Interior layer: corridors, elevators, and tenant spaces
Goals: segmentation, surveillance, and rapid intervention.
- Zoned access: elevator dispatch by credential, floor-restricted badges, and interlocked doors on sensitive corridors (IT rooms, finance, Rx storage).
- Video coverage with response: intelligent video analytics, privacy-safe rules, and live monitoring with dispatchable response—so alarms trigger an action plan, not just a recording.
- Alarms and duress: door-prop alarms, glass-break sensors, hold-up buttons for cash handling or reception desks.
- Operations playbooks: post orders that spell out what officers do per alarm type: verify, contain, escalate, and document.
People layer: trained eyes and decisive action
Goals: skilled prevention and fast resolution.
- Staff training: awareness for employees (challenge-and-escort culture, tailgating prevention), plus active threat and de-escalation drills for frontline teams.
- Security officer program: match risk to posture—unarmed for customer-facing lobbies, semi-armed for elevated-risk evening operations, armed for high-value or high-threat zones—with clear SOPs and escalation thresholds.
- Post orders by site profile: daytime retail differs from after-hours corporate; write orders that reflect risk at each hour and location.
Industry resources for commercial facilities planning and training are maintained by CISA; their sector publications and guides can help benchmark your plan.
Technology layer: integrate, don’t just accumulate
Goals: connect signals into decisions.
- Unified platform: tie access control, video, alarms, LPR, and intercoms into a single dashboard that reduces “alarm fatigue” and routes incidents to the right team.
- Analytics with guard tour data: heat-map incidents, near-misses, and patrol paths; adjust routes, lighting, and staffing accordingly.
- Cyber-physical convergence: protect cameras, cards, and controllers like any other IT asset (patching, segmentation, MFA). CISA highlights the value of converged programs for resilience.
Response layer: when seconds matter
Goals: clear roles, practiced timing, and documented outcomes.
- Dispatch matrix: who responds to which alarm, in what sequence, with what equipment (radio channels, keys, lock-down tools).
- SRT and mobile units: define conditions for elevating to a special response team (SRT) or calling mobile patrol backup; use time-to-scene KPIs.
- After-action loop: incident report → root-cause review → control changes (lighting, landscaping, badge rules) → training updates.
- Continuity playbooks: power, HVAC, and network dependencies noted with backup steps (e.g., generator fuel checks, fail-secure door states).
How to build your layered plan (step-by-step)
- Map your crown jewels. Identify critical assets: people, cash points, pharmaceuticals, server rooms, IP.
- Conduct a risk assessment. Use a structured method (likelihood × impact) to score scenarios and pick controls with the best risk-reduction ROI. NIST Computer Security Resource Center
- Design rings of protection. Perimeter → entry → interior → people → technology → response. Decide how each ring detects, delays, and communicates. ASIS International
- Write measurable post orders. Plain language tasks, escalation triggers, and service-level targets (acknowledge in 60s, arrive in 5–7 min, etc.).
- Integrate systems. Choose platforms that share events and identities; standardize nomenclature (doors, cameras, zones) for clean reporting.
- Drill and iterate. Table-top first, then live tests. Close every drill with lessons learned and a configuration or training change.
Example: blending patrols, access, and cameras in retail-office mixed use
A coastal retail-office development faces late-night trespass, parking break-ins, and early-morning deliveries. The layered plan:
- Perimeter: better sightlines, LED lighting, and LPR at ingress points.
- Entry: dock pre-registration with time-bound QR codes; lobby officer 24/7 with de-escalation training.
- Interior: camera analytics for loitering after 10 p.m.; door-prop alerts to mobile units.
- People: randomized mobile patrols during closing and opening windows; merchant safety briefings each quarter.
- Technology: unified platform sends verified alarms directly to dispatch; SRT auto-paged for weapon indicators.
- Response: arrival-time KPIs tracked weekly; incidents tagged to root causes (lighting outage, door maintenance, policy gaps).
For services that implement the technology-plus-people layers end to end, see our page on Commercial Security Services—it outlines patrol options, access control programs, and live monitoring that slot directly into a layered design.
Why partner with City Wide Protection Services
- Proven response: 24/7 dispatch, mobile units, and special response teams coordinated by clear SLAs.
- Integrated approach: access control, live camera monitoring with response, and patrols—architected as layers, not silos.
- California-ready: programs built around local operating realities and stakeholder expectations for commercial real estate.
Let’s design your Layered Security for Commercial Properties. Call (888) 205-4242 or email [email protected] to schedule a site walk and risk review.